
Researchers find two npm packages hiding malware inside Ethereum smart contracts
The campaigns showed inflated start, commits and contributors, to appear trustworthy
23 crypto malware campaigns in open-source repos were reported last year
Ethereum, the backbone of crypto apps and DeFi projects, is increasingly being used as a tool for cyberattacks.
Researchers at ReversingLabs have found two npm packages that hid malicious commands inside Ethereum smart contracts, marking a new twist in software supply chain attacks.
Read on to know how this was carried out.
Simple Packages With Hidden Malwares
The two packages, colortoolsv2 and mimelib2, looked like harmless tools, but they secretly pulled in downloader malware. These packages are part of a broader, sophisticated campaign spreading across npm and GitHub.
In July, RL discovered colortoolsv2 using blockchain to deliver malware. It was quickly removed, but a near-identical package called mimelib2 soon appeared with the same malicious code.
Both npm packages were minimal and carried only the malware, while their GitHub repositories were made to look polished and reliable to fool developers.
Using Smart Contracts as a Stealth Tool
What makes this campaign stand out is how the attackers used Ethereum smart contracts to hide malicious URLs.
Colortoolsv2 appeared to be a basic npm package with only two files. Hidden inside was a script that downloaded additional malware from a command-and-control server. Usually, malware campaigns hardcode URLs into their code, which makes them easier to detect.
In this case, the URLs were stored inside Ethereum smart contracts, making it much harder to track and shut down the attack.
“That’s something we haven’t seen previously, and it highlights the fast evolution of detection evasion strategies by malicious actors who are trolling open source repositories and developers,” the researchers said.
Hackers Are Getting More Creative
This attack is part of a growing trend where hackers are finding new ways to deliver malware. In 2023, some Python packages hid malicious URLs inside GitHub Gists, and in 2022, a fake Tailwind CSS npm package stored malware links behind trusted platforms like Google Drive and OneDrive.
- Also Read :
- Who’s Really Driving Bitcoin? Asia Or U.S
- ,
How GitHub Was Used as Trap
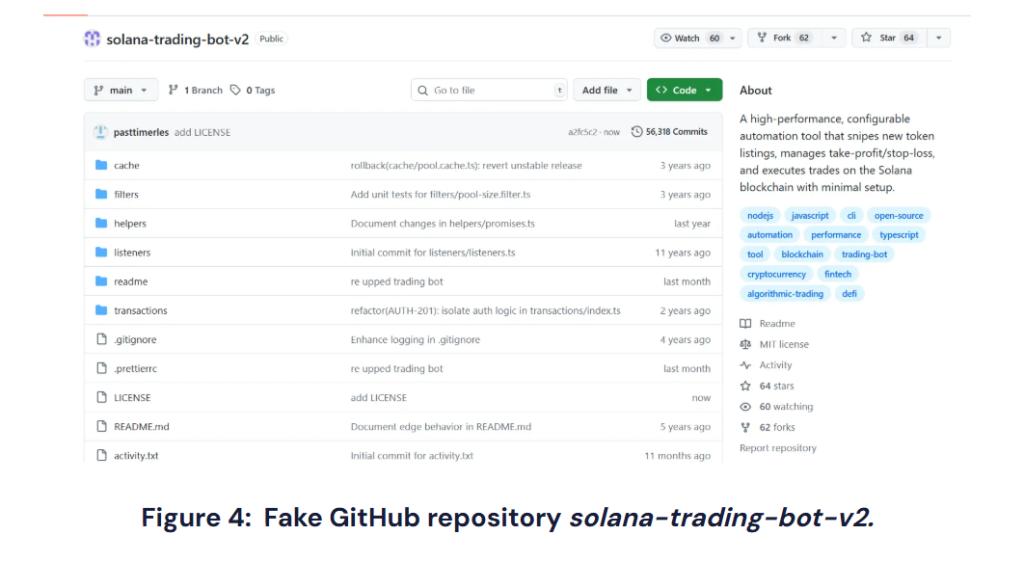
The attackers also built fake GitHub repositories to make their campaign more convincing.
Attackers set up fake repositories tied to the colortoolsv2 package, posing as crypto trading bots. These projects looked convincing, with thousands of commits, active contributors, and plenty of stars.
But the activity and popularity were faked to trick developers into downloading poisoned code.
This campaign didn’t stop with solana-trading-bot-v2. Other repos like ethereum-mev-bot-v2, arbitrage-bot, and hyperliquid-trading-bot also showed fake commits and activity, though less convincing.
Last year saw 23 campaigns where attackers planted malicious code in open-source repos, including the ultralytics PyPI crypto miner and an April 2025 malware attempt on local crypto tools.
Never Miss a Beat in the Crypto World!
Stay ahead with breaking news, expert analysis, and real-time updates on the latest trends in Bitcoin, altcoins, DeFi, NFTs, and more.
For developers, this is a reminder to carefully vet open-source libraries. Stars, downloads, and activity do not guarantee trust. Both code and maintainers need to be thoroughly reviewed before integration.
FAQs
Attackers are hiding malicious download URLs inside Ethereum smart contracts to evade detection, a new evasion tactic in software supply chain attacks.
The packages colortoolsv2 and mimelib2 contained hidden malware that downloaded additional payloads from attackers’ servers.
Storing malicious URLs on-chain makes attacks harder to detect and shut down compared to traditional hardcoded links in software.
Trust with CoinPedia:
CoinPedia has been delivering accurate and timely cryptocurrency and blockchain updates since 2017. All content is created by our expert panel of analysts and journalists, following strict Editorial Guidelines based on E-E-A-T (Experience, Expertise, Authoritativeness, Trustworthiness). Every article is fact-checked against reputable sources to ensure accuracy, transparency, and reliability. Our review policy guarantees unbiased evaluations when recommending exchanges, platforms, or tools. We strive to provide timely updates about everything crypto & blockchain, right from startups to industry majors.
Investment Disclaimer:
All opinions and insights shared represent the author's own views on current market conditions. Please do your own research before making investment decisions. Neither the writer nor the publication assumes responsibility for your financial choices.
Sponsored and Advertisements:
Sponsored content and affiliate links may appear on our site. Advertisements are marked clearly, and our editorial content remains entirely independent from our ad partners.








