
Aperture Finance exploit drained $3.67M after attackers targeted vulnerable V3 and V4 smart contracts.
Hack-linked wallets later moved 1,242 ETH worth $2.4M into Tornado Cash for laundering purposes.
Security teams urged users to revoke ERC20 and liquidity position approvals tied to compromised contract addresses.
DeFi platform Aperture Finance has suffered a major security breach, losing about $3.67 million in a smart contract exploit. Blockchain security firm PeckShieldAlert shows the hacker is actively moving stolen funds through Tornado Cash, a privacy-mixing service.
The activity has raised new concerns about fund recovery and how the actual hack happened.
How The Aperture Finance Exploit Happened
According to PeckShieldAlert, the Aperture Finance hack happened on January 25, 2026, due to a weakness in its V3 and V4 smart contracts, combined with existing user token approvals.
In DeFi platforms, users often permit contracts to move their ERC-20 tokens or liquidity position NFTs so trades and strategies can run automatically. But in this case, the exploiter found a flaw in how the contract handled those permissions and function calls.
Instead of breaking wallets or stealing private keys, the attacker used the contract’s own logic to trigger unauthorized asset transfers.
Because many users had already granted approvals, the attacker could move funds without needing new signatures. This allowed them to drain assets tied to approved tokens and liquidity positions.
Funds Moved to Tornado Cash After Hack
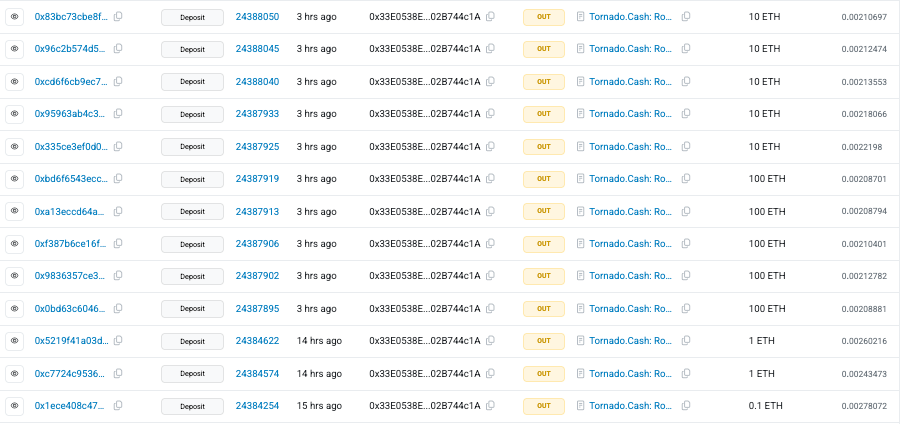
And all this led to the extraction of $3.67 million in value, the attacker converted a large share into ETH, and sent about 1,242 ETH to Tornado Cash to hide the trail.
Attackers often use mixing services like Tornado Cash to hide the origin of stolen crypto and make tracking more difficult. The funds were sent in multiple small transactions, including batches of 10 ETH and 100 ETH, a common method used to avoid attention.
Users Asked to Revoke Token and NFT Approvals
Following the exploit, the Aperture Finance team released an emergency notice and shared a list of affected contract addresses. And also warned users to urgently revoke both ERC-20 token approvals and ERC-721 liquidity position approvals tied to the risky addresses.
Wallet approvals allow smart contracts to move user funds, and if left active, they can be abused after a contract is compromised.
Never Miss a Beat in the Crypto World!
Stay ahead with breaking news, expert analysis, and real-time updates on the latest trends in Bitcoin, altcoins, DeFi, NFTs, and more.
FAQs
Hackers exploited a weakness in the platform’s smart contracts, using existing user token approvals to move assets without stealing private keys.
Users should immediately revoke all token and liquidity position approvals linked to the affected contract addresses to prevent further losses.
Services like Tornado Cash obscure transaction trails, making it difficult to track and recover stolen cryptocurrency after a hack.
No. The exploit abused smart contract permissions; your private keys remain secure, but your approved funds were at risk.
Trust with CoinPedia:
CoinPedia has been delivering accurate and timely cryptocurrency and blockchain updates since 2017. All content is created by our expert panel of analysts and journalists, following strict Editorial Guidelines based on E-E-A-T (Experience, Expertise, Authoritativeness, Trustworthiness). Every article is fact-checked against reputable sources to ensure accuracy, transparency, and reliability. Our review policy guarantees unbiased evaluations when recommending exchanges, platforms, or tools. We strive to provide timely updates about everything crypto & blockchain, right from startups to industry majors.
Investment Disclaimer:
All opinions and insights shared represent the author's own views on current market conditions. Please do your own research before making investment decisions. Neither the writer nor the publication assumes responsibility for your financial choices.
Sponsored and Advertisements:
Sponsored content and affiliate links may appear on our site. Advertisements are marked clearly, and our editorial content remains entirely independent from our ad partners.








