
CertiK detected a $2.3 million crypto theft using its Skylens on-chain monitoring system.
Two wallets sent stolen funds to one malicious address, confirming a coordinated crypto hack.
Victims sent on-chain messages requesting negotiation, confirming funds were stolen, not willingly transferred.
Blockchain security company CertiK has issued an important warning after detecting a suspicious on-chain incident that led to the loss of nearly $2.3 million in digital assets.
According to CertiK, the suspicious activity was found using its Skylens monitoring system, which tracks unusual movements on the blockchain.
How the $2.3 Million Crypto Hack Happened
According to the CertiK report, there were two wallets involved in the attack. One wallet sent around $1.8 million, while the second wallet sent about $506,000. Both transfers went to the same unknown wallet, which was later marked as malicious.
This means the money was likely stolen, not sent by choice.
After receiving the stolen money, the attacker quickly moved the funds into Tornado Cash, a crypto privacy tool. Tornado Cash is often used to hide transaction trails, making it very hard to track or recover stolen funds.
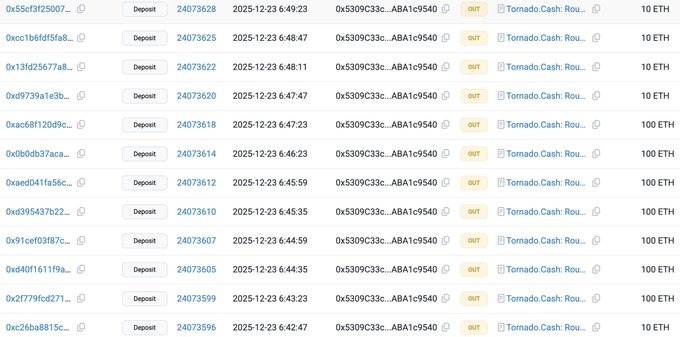
Blockchain data shows multiple Ethereum transfers, including small and large amounts like 10 ETH and 100 ETH, being sent through Tornado Cash within minutes. This fast movement is a common sign of a planned attack.
- Also Read :
- DeFi Protocol USPD Loses $1 Million in “CPIMP” Attack
- ,
The Victim asks for Negotiation
What makes this case unusual is what happened next. CertiK’s data shows that both compromised wallets sent an on-chain message to the receiving address, asking whether negotiation was possible.
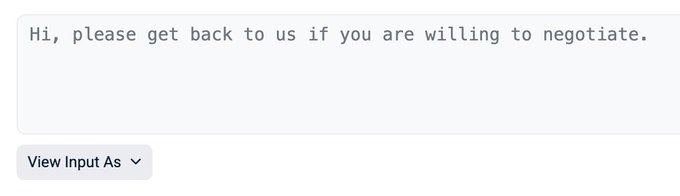
This suggests the transfers were not intentional trades, but likely the result of a security breach where wallet access was lost.
Sharp Warning For Crypto Users
This incident once again highlights the growing risks around wallet security. Even without smart contract exploits, attackers can drain funds using compromised private keys, phishing links, or malicious approvals.
Meanwhile, some experts have started closely monitoring and flagging the wallet address, even though recovering the stolen funds may not be possible.”
Never Miss a Beat in the Crypto World!
Stay ahead with breaking news, expert analysis, and real-time updates on the latest trends in Bitcoin, altcoins, DeFi, NFTs, and more.
FAQs
Retail users, traders, and protocols interacting with compromised wallets can face indirect losses if funds move through shared platforms. Such incidents also undermine confidence in self-custody, a core principle of crypto adoption.
Once assets pass through a mixer, tracing becomes significantly harder, limiting the ability of exchanges or law enforcement to freeze funds. Intervention is most effective before mixing occurs.
Security firms and analysts continue monitoring related addresses for future movements. The affected parties often rotate wallets, review access points, and strengthen operational security to prevent repeat breaches.
Trust with CoinPedia:
CoinPedia has been delivering accurate and timely cryptocurrency and blockchain updates since 2017. All content is created by our expert panel of analysts and journalists, following strict Editorial Guidelines based on E-E-A-T (Experience, Expertise, Authoritativeness, Trustworthiness). Every article is fact-checked against reputable sources to ensure accuracy, transparency, and reliability. Our review policy guarantees unbiased evaluations when recommending exchanges, platforms, or tools. We strive to provide timely updates about everything crypto & blockchain, right from startups to industry majors.
Investment Disclaimer:
All opinions and insights shared represent the author's own views on current market conditions. Please do your own research before making investment decisions. Neither the writer nor the publication assumes responsibility for your financial choices.
Sponsored and Advertisements:
Sponsored content and affiliate links may appear on our site. Advertisements are marked clearly, and our editorial content remains entirely independent from our ad partners.







